How to Protect Citrix Gateway and AAA using Web Application Firewall
This is a step-by-step guide on how to enable Web Application Firewall on NetScaler Gateway and NetScaler AAA. This is a new capability introduced by Citrix NetScaler starting with version 14.1 build 21.57. It is a new streamlined process compared to the creative methods that were devised in the past.
NetScaler (a.k.a Citrix NetScaler or Citrix ADC) has offered the Web App Firewall (WAF) for many years in order to protect Web applications but not really Gateway functionality. This was a feature that you could purchase as a standalone feature or as part of the Premium/Platinum editions. The Cloud Software Group that now owns Citrix and NetScaler has been adjusting their licensing models later so it would be more appropriate to consult with sales on available options. This WAF capability for NetScaler Gateway and NetScaler AAA virtual servers is now included in every edition going forward.
Enable WAF for NetScaler Gateway and NetScaler AAA
The process to enable the WAF capability is very straightforward:
- Enable the feature
- Enable Analytics (optional) but we assume that we will proceed with it.
On the GUI
Navigate to Configuration, System, Settings.
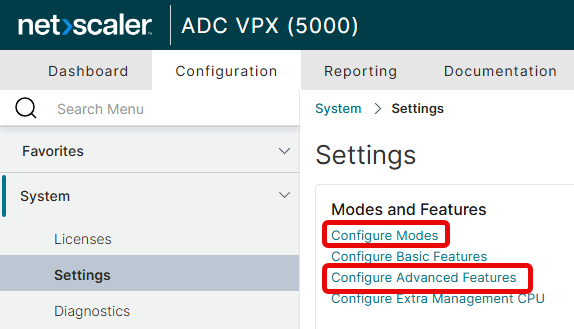
Enable the ULFD mode.
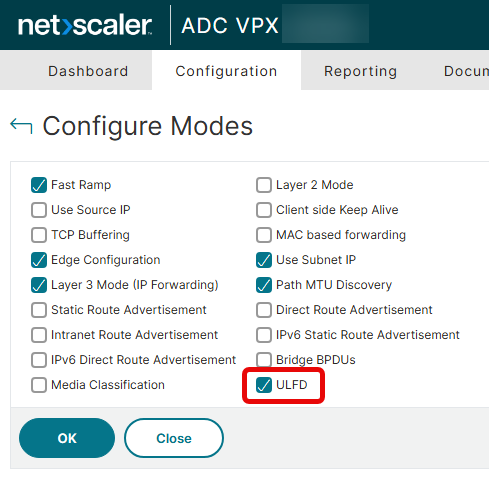
Enable the AppFlow feature.
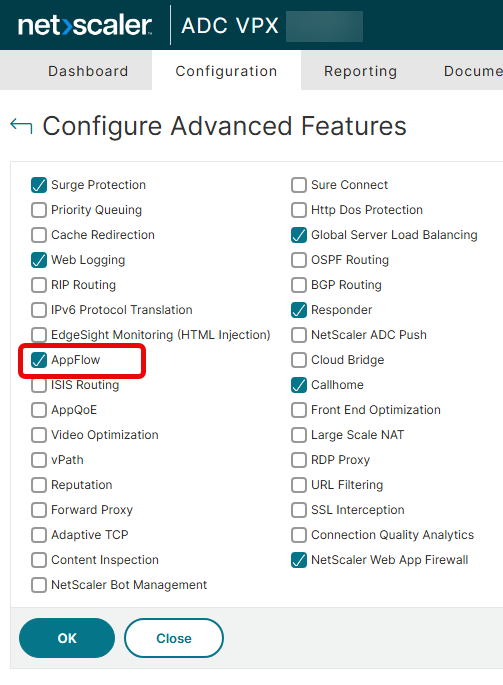
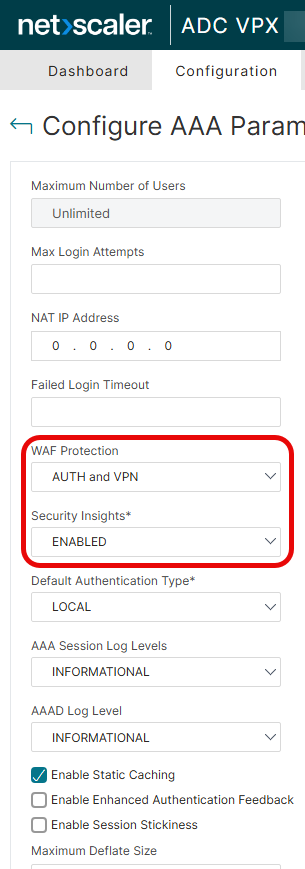
Navigate to Security, AAA-Application Traffic, change Authentication AAA Settings.
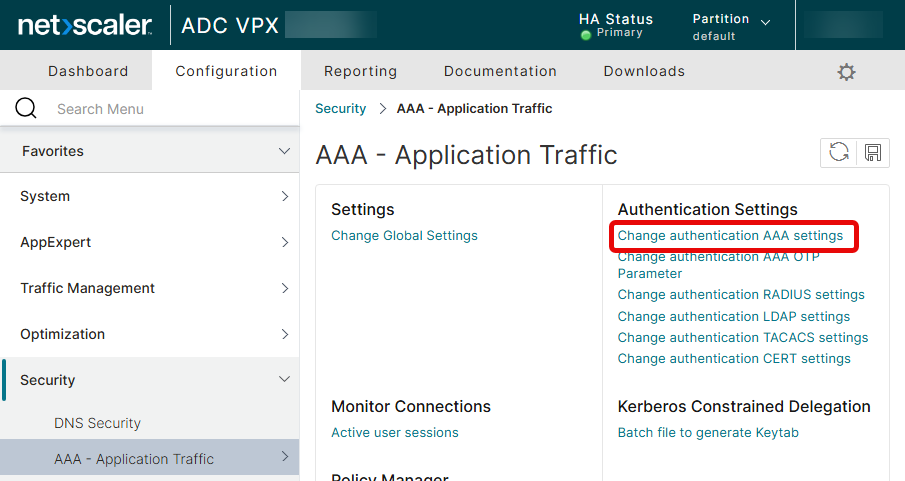
Select the WAF Protection and configure it to AUTH and VPN.
On the CLI
# Enable protection on gateway and AAA and enable Security Insights
set aaa parameter -wafProtection AUTH VPN
set aaa parameter -securityInsights ENABLED
# The below three commands may be already enabled if you had already utilized NetScaler Console to enable Analytics for some other virtual server
en ns mode ULFD
en ns feature appflow
# NetScaler Console automatically generates the name of the collector as af_collector_logstream_collectorIP but you can use any name if you manually perform this on the NetScaler appliance
add appflow collector af_collector_logstream_10.10.10.99 -IPAddress 10.10.10.99 -port 5557 -Transport logstream
# send analytics
set analytics profile ns-aaa-vpn-appfw-analytics-profile -collectors af_collector_logstream_10.10.10.99 -type securityinsight
# save configuration
save ns config
Configure NetScaler Console Analytics
Although you do not have to enable Security Insights for the WAF functionality, enabling logging is very important in securing an environment. The process below assumes that you already have implemented NetScaler Console on-premises or utilize the NetScaler Console service (cloud-based).
Tip
The latest version of NetScaler Console as of this writing, does not require Virtual Server licensing.
On the NetScaler Console
Navigate to Infrastructure, Instances, NetScaler and select the NetScaler instance you want to configure analytics. This will show all available servers on that NetScaler appliance. Right-click the gateway that you want to configure analytics to display the available options.
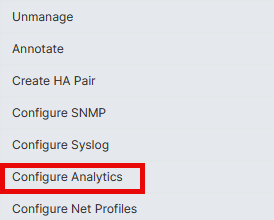
On the Edit Analytics, enable the WAF Security Violations.
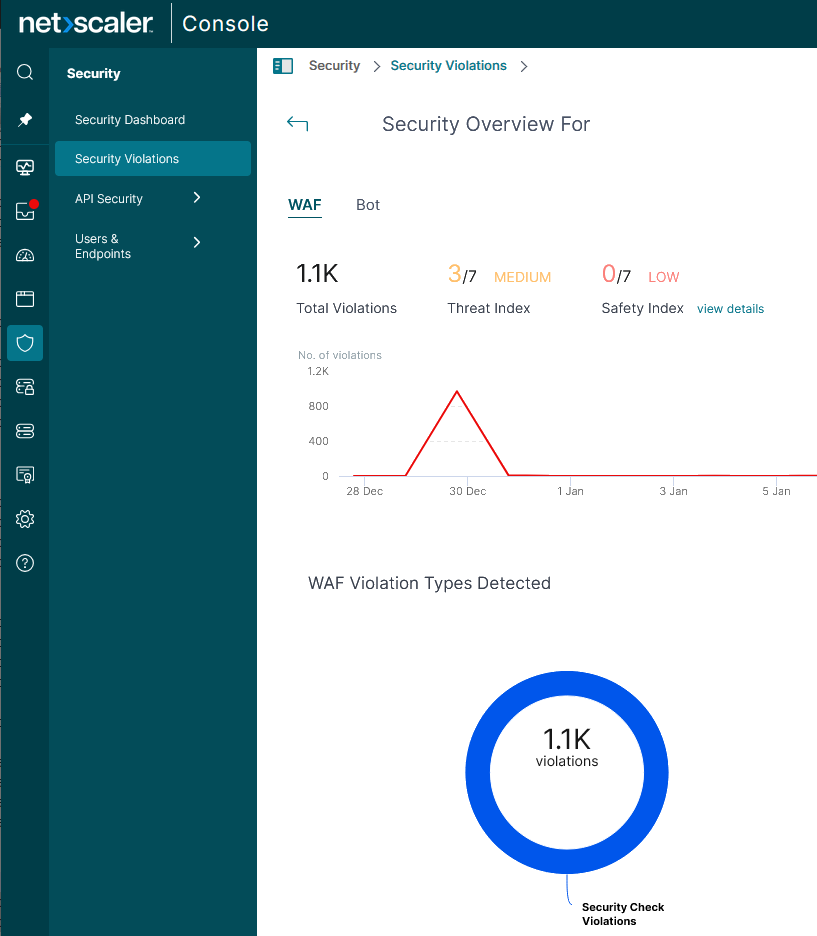
Once data has been collected, you will be able to view Security Violations from within NetScaler Console, Security, Security Violations.
Info
This WAF capability is performing checks against “REST API Schema Validation” and this can be seen on the NetScaler appliance, Security, NetScaler Web App Firewall, Profiles, ns-vpn-default-appfw-profile, Security Checkes. You could possibly enable additional checks but additional expertise will be required.
Related links for NetScaler WAF
Official NetScaler documentation on Web App Firewall protection for VPN virtual servers and authentication virtual servers
Official NetScaler product page for Web Application Firewall