Guide to Delegating Control for Domain Join Operations in AD
This is a step-by-step guide for Active Directory delegate control to allow a specific group to join computers to the domain by delegating the appropriate permissions. This involves granting the group the rights to create computer objects in a specified Organizational Unit (OU). Below are the exact steps to accomplish this:
Prerequisites for Delegate Control
- Administrative Access: Ensure you have domain administrator privileges.
- Group Created: The group to which you want to assign permissions should already exist.
Warning
Although you can delegate permissions to a user, avoid doing so as it complicates management and increases security risks.
Step-by-Step Instructions for delegation
- Open Active Directory Users and Computers (ADUC)
- On a Domain Controller or Admin Workstation:
- Click on the Start menu.
- Type “Active Directory Users and Computers” and press Enter.
- Alternatively, run dsa.msc.
- Enable Advanced Features
- In the ADUC console:
- Click on “View” in the menu bar.
- Ensure “Advanced Features” is checked.
- This enables additional options required for delegation.
- Navigate to the Organizational Unit (OU)
- In the left pane:
- Expand your domain (e.g., yourdomain.com).
- Locate and select the OU where you want users to add computers.
- Note: You can create a new OU specifically for computers joined by this group if desired.
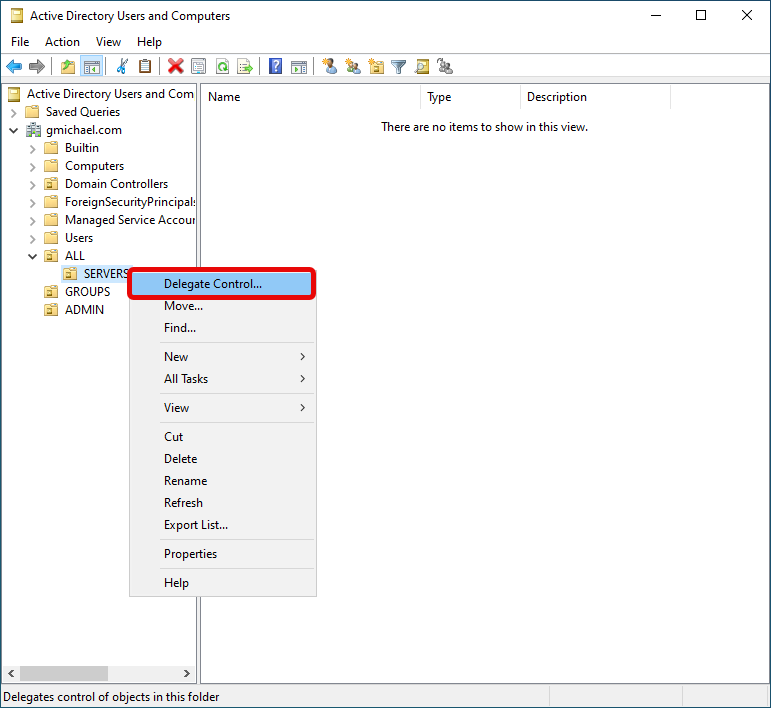
- Delegate Control to the Group
Right-click on the selected OU.
Choose “Delegate Control…”.
- This opens the Delegation of Control Wizard.
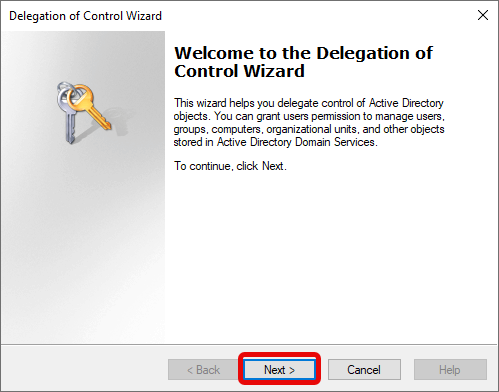
- Delegation of Control Wizard
a. Welcome Screen
- Click “Next”.
b. Select Users or Groups
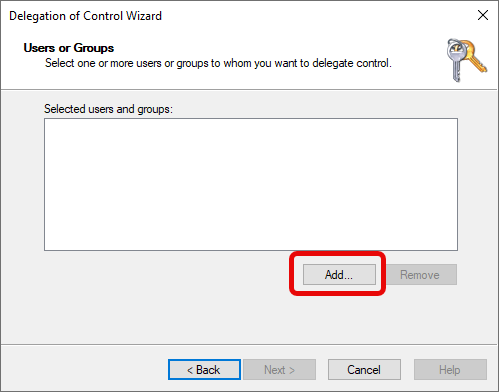
Click “Add”.
In the “Enter the object names to select” field:
- Type the name of the group you’re delegating permissions to.
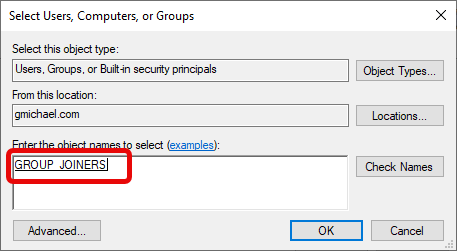
Click “Check Names” to verify.
Click “OK”.
Confirm the group is listed in “Selected users and groups:”.
Click “Next”.
c. Choose Tasks to Delegate
Select “Create a custom task to delegate”.
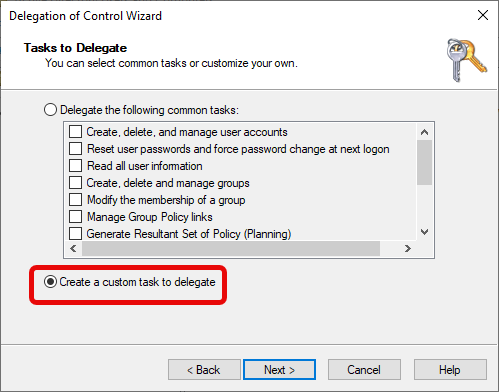
Click “Next”.
d. Active Directory Object Type
Choose “Only the following objects in the folder”.
In the objects list, check “Computer objects”.
Below the list, check:
- “Create selected objects in this folder”.
- (Optional) “Delete selected objects in this folder” if you want the group to also have deletion rights.
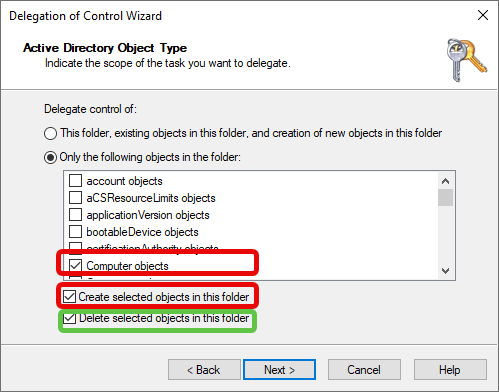
Click “Next”.
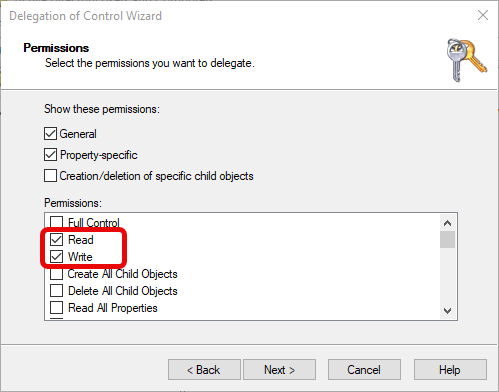
e. Permissions
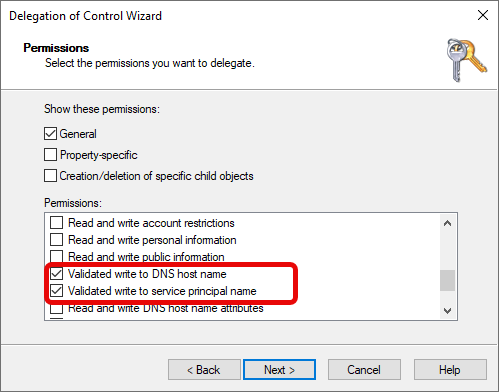
In the permissions list, check the following permissions:
- General Permissions:
- “Read”
- “Write”
- Property-Specific Permissions:
- “Reset Password”
- “Validated write to DNS host name”
- “Validated write to service principal name”
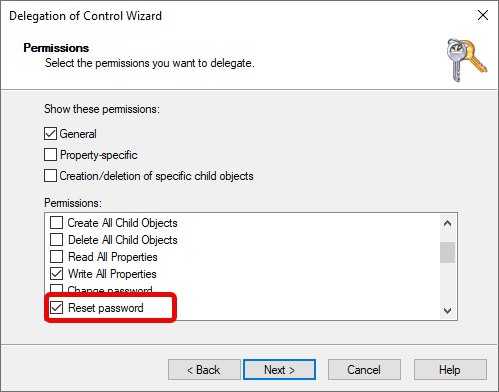
- General Permissions:
Warning
Alternatively, for broader permissions, you can check “Full Control” but this is not recommended due to security considerations.
- Click “Next”.
f. Completing the Delegation of Control Wizard
Review the selections.
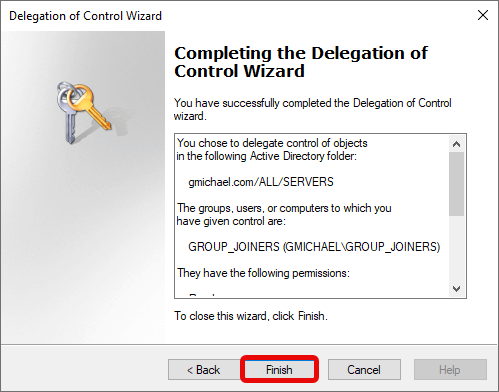
Click “Finish”.
Additional Configuration
Adjust the Machine Account Quota (Optional)
By default, authenticated users can join up to 10 computers to the domain. To remove this limit for the group:
- Option A: Using ADSI Edit
- Open ADSI Edit:
- Run adsiedit.msc.
- Connect to the Default Naming Context.
- Right-click on the domain root (e.g., DC=yourdomain,DC=com) and select “Properties”.
- In the “Attributes” list, locate ms-DS-MachineAccountQuota.
- Modify its value:
- Set to 0 to prevent users from joining computers outside of delegated permissions.
- Modify its value:
- Click “OK”.
- Open ADSI Edit:
- Option B: Using PowerShell
- Open PowerShell with administrative privileges.
- Run the following command:
dsmod domain "DC=yourdomain,DC=com" -rmachineaccountquota 0
Verify Delegate Control Permissions
- Test with a User Account:
- Ensure that a user in the group can join a computer to the domain.
- Verify that they cannot perform unintended administrative actions.
Important Notes about Delegation
- Security Best Practices:
- Principle of Least Privilege: Only grant necessary permissions.
- Regular Audits: Periodically review group memberships and delegated permissions.
- Limiting Scope:
- Specific OU: Delegating permissions on a specific OU limits where computers can be added.
- Separate OUs: Consider creating separate OUs for different departments or purposes.
Summary of Delegate Control
By delegating the necessary permissions to a group on a specific OU, you enable its members to join computers to the domain without granting them full administrative rights. This approach enhances security and streamlines domain join operations.
References on Permissions and Best Practices for Delagation
Microsoft Docs - Delegate Permissions to Join a Computer to the Domain